Authentication is important thing to consider when we think of automating deployment or any task that needs to access SharePoint from CI/CD pipeline. In this article we will see how we can authenticate to SharePoint using certificate through PnP PowerShell.
I already have an Azure App with necessary permission (in my case – SharePoint, Permission Name: AllSites.FullControl – Type: Application) to access my SharePoint sites.
We need a certificate that we can upload in our Azure App and .pfx file (personal exchange information) that needs to be uploaded to Azure DevOps which acts as a private key for the certificate.
Generate Certificate
PnP PowerShell provides a cmdlet that can generate both .pfx and .cer files, – https://pnp.github.io/powershell/cmdlets/New-PnPAzureCertificate.html
New-PnPAzureCertificate
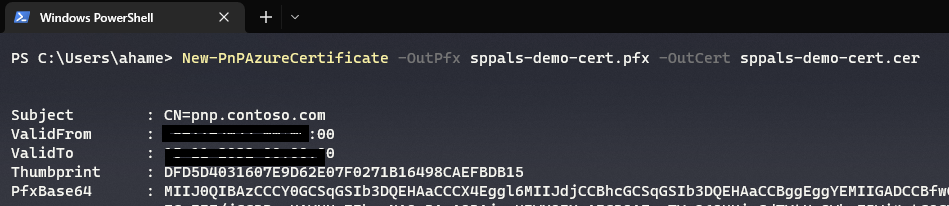
With the above commands it generated two files – .cer and .pfx. We need both the files, where .cer file should be uploaded to Azure App and .pfx file should be added to Azure DevOps secure file, and its explained in detail as follows,
Upload .cer file to Azure App and .pfx file to Azure DevOps
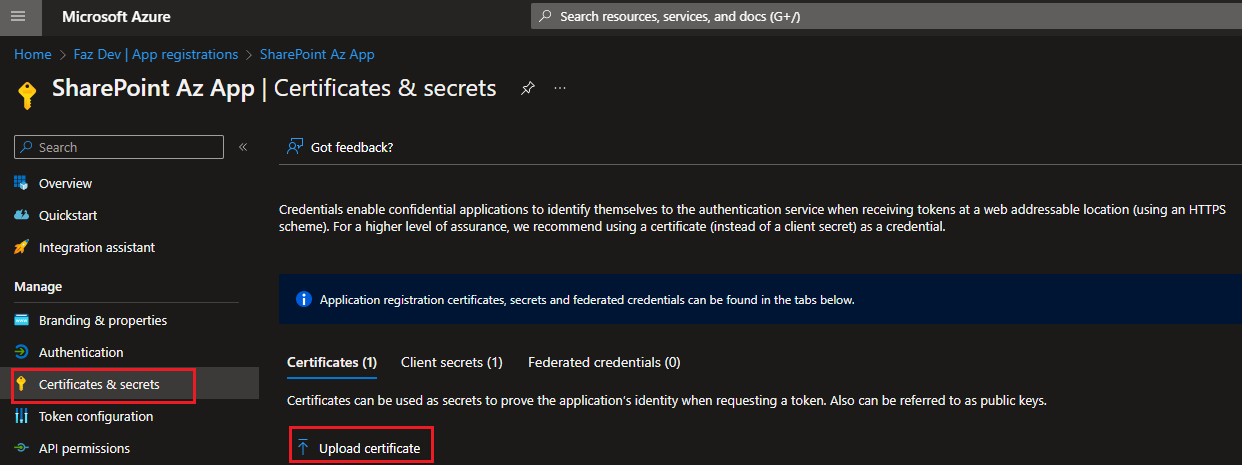
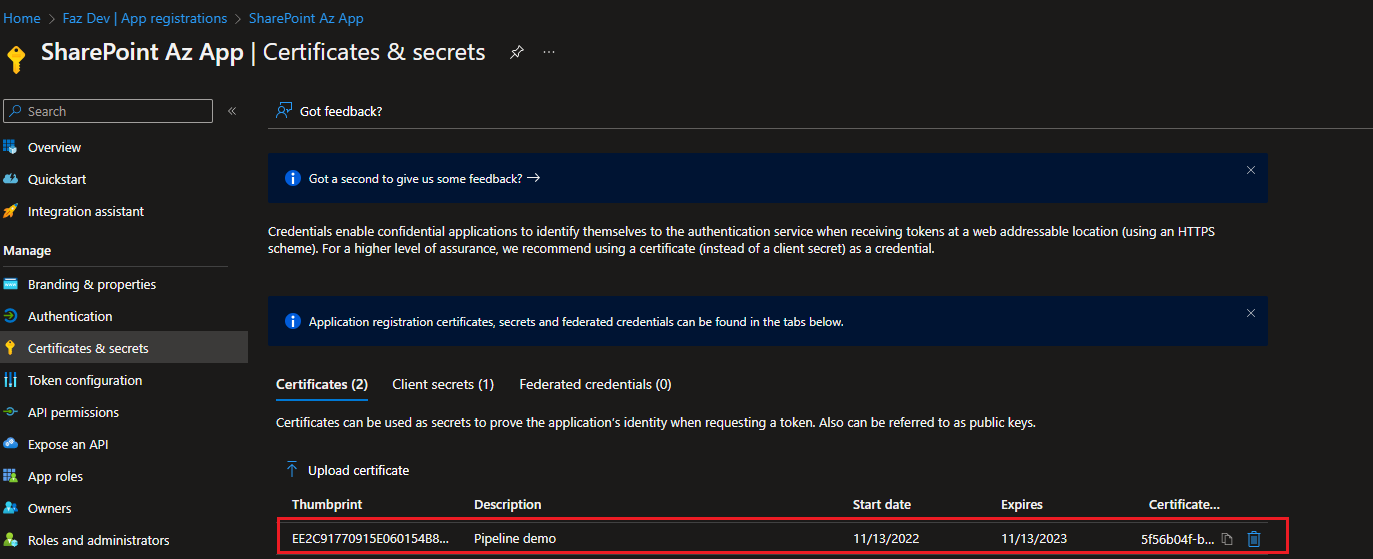
In the above section we generated .cer file and the file needs to be uploaded into Azure App as shown in below screenshots
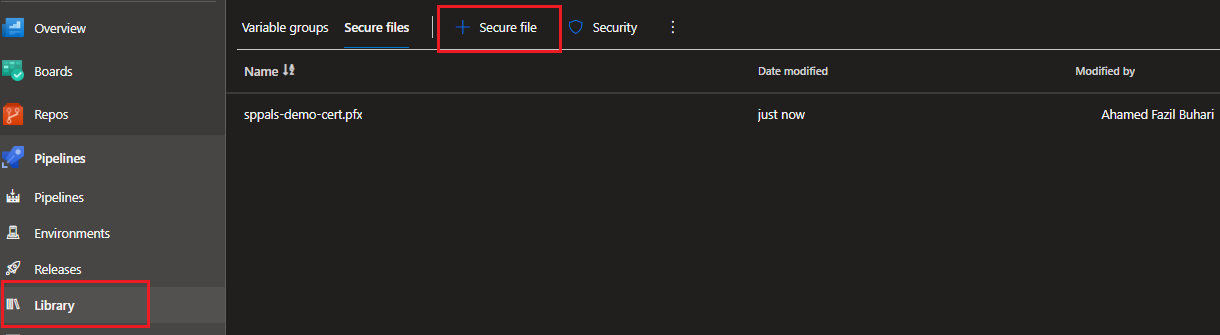
In Azure DevOps under Pipelines section, select Library. In the library we can have variable groups, and secure files. We need to keep our .pfx file some where secure in Azure DevOps, so we can upload it here.
Connect to SharePoint in Azure DevOps Release Pipeline
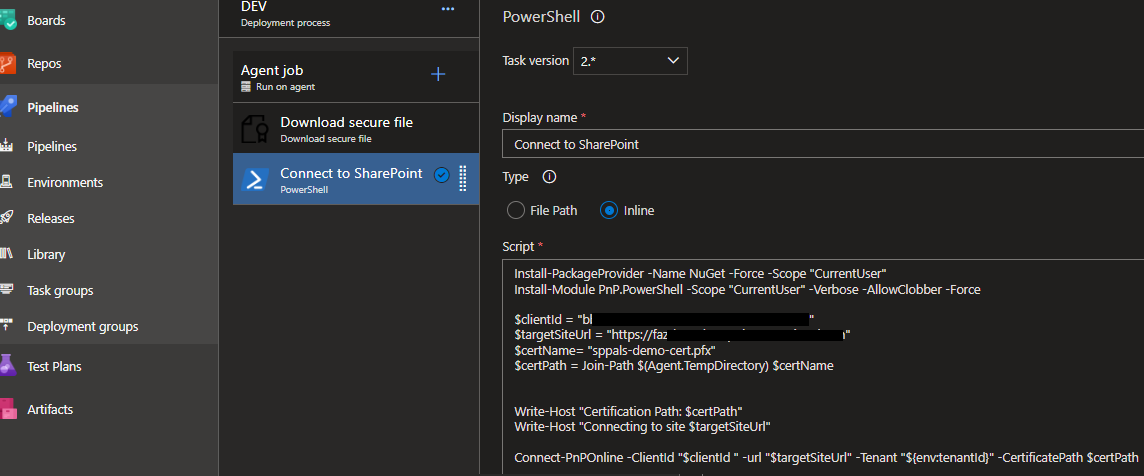
Here I am connecting to SharePoint from Release pipeline by having couple of tasks. We can use “Download secure file” task from Microsoft to download our .pfx file from library and then its followed by a PowerShell task where we can have PnP command to connect to SharePoint using certification path, as shown below.
Connect-PnPOnline -ClientId "" -Url "" -Tenant "" -CertificationPath ""
In the PowerShell, we need to provide clientId (Azure App Id), SharePoint site URL, tenant Id and .pfx file path. Now you can access SharePoint by using certification in your pipeline 🙂
Happy Coding
Fazil

Leave a comment