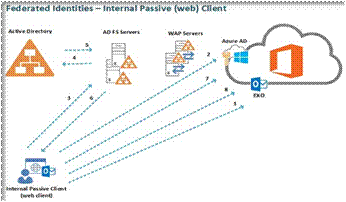
Let’s talk more on Federation model and also on the modern authentication for SharePoint online now. In the case of federated environment, once you sign with your organization account to SharePoint online and if your account is federated, Web client redirects the request from login.microsoft.com to On-premises ADFS/other 3rd party federation engine.
The Azure AD authentication endpoint will detect if the particular account is federated if so, does another redirection to the internal federation service (which can be either ADFS or anything) Federation service requires the client to authenticate. Once authenticated, federation services will retrieve the necessary claims related information from Active Directory and provide the web client with a token holding the claims about the user. The client will present the token to Azure AD and after successful authentication, the web client will be redirected back to Microsoftonline.com.
To understand more on how user profile synchronization works, please refer
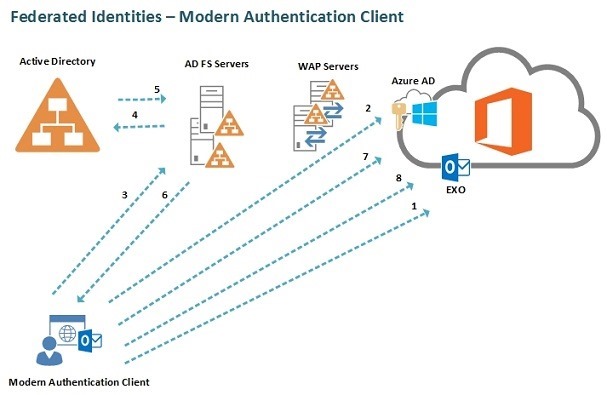
Now let’s see what is modern authentication is all about:
Though this has got nothing to do in SharePoint online, this is mainly for office 365 Apps.
Modern authentication brings Active Directory Authentication Library (ADAL)-based sign-in to Office client apps across platforms. This enables sign-in features such as Multi-Factor Authentication (MFA), SAML-based third-party Identity Providers with Office client applications, smart card and certificate-based authentication, and it removes the need for Outlook to use the basic authentication protocol.
By enabling ADAL for Office client applications, they will use an in-application browser control to render the Azure AD sign in experience in the same fashion as browser-based Office 365 clients like the Outlook on the Web (OotW). ADAL based OAuth authentication works for federated as well as non-federated scenarios.
To know more on session timeout for office 365 services please refer (this might differ based on our organization internal federation system setting)

Leave a comment