In the recent articles, we saw how to get the ClientContext using the UserName and password. In this article, let us see how to create the ClientContext using any of the APP’s ClientID and ClientSecret ID. I know, this may not be necessary in all the scenarios. But let me explain the detailed scenario, why we required this also. That will help the readers to understand the requirement clearly.
We were working on a Migration Project, in which we need to continuously hit the Office 365 site in a very high frequency. At that time, the account which we are using for migration is being throttled by Microsoft. i.e., We cannot use the account for the next 10-20 mins. Hence, we were facing a lot of issues regarding this. (Planning to write a separate article for throttling. Let us see in the upcoming articles regarding the detailed throttling issues). In that case, we were trying with an APP model. i.e., Instead of using a service account, why cant we try with the Installed APP’s context.
With this background, hope we remember, how to create a PHA for Office 365. If not, please have a refresh HERE.
The important parameters to be noted are,
1. ClientID
2. ClientSecretID
3. RealmID
We can get the ClientID and ClientsecretID from the Web.Config of our APPs project.
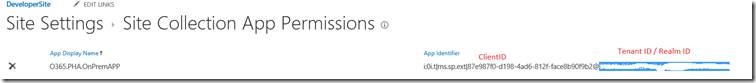
And the Realm ID is nothing but the tenant ID. The tenant ID can be taken from the app principals.aspx.
https://*******.sharepoint.com/sites/developersite/_layouts/15/appprincipals.aspx
The piece of Code is as follows.
namespace Console.Office365
{
using Microsoft.SharePoint.Client;
using Newtonsoft.Json.Linq;
using System;
using System.Collections.Generic;
using System.IO;
using System.Linq;
class Program
{
static void Main(string[] args)
{
CreateClientContextUsingClientIDandClientSecret();
}
public static void CreateClientContextUsingClientIDandClientSecret()
{
Uri webUri = new Uri("https://********.sharepoint.com/sites/developersite");
var SharePointPrincipalId = "00000003-0000-0ff1-ce00-000000000000";
var token = TokenHelper.GetAppOnlyAccessToken(SharePointPrincipalId, webUri.Authority, null).AccessToken;
var ctx = TokenHelper.GetClientContextWithAccessToken(webUri.ToString(), token);
Web web = ctx.Web;
ctx.Load(web);
ctx.Load(web.Lists);
ctx.ExecuteQueryRetry();
}
}
}
And on the APP.Config insert the below entries.
<appSettings>
<add key="ClientId" value="********" />
<add key="ClientSecret" value="***************" />
<add key="Realm" value="<<The one which we got from appprincipals.aspx>>" />
</appSettings>
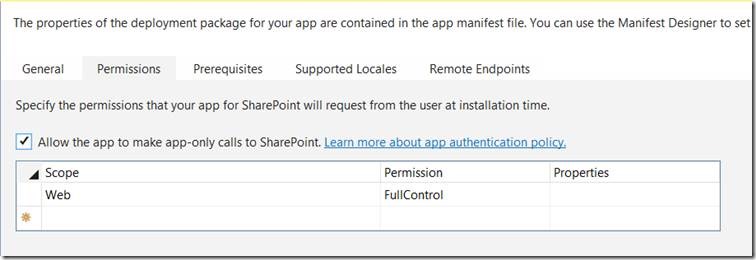
One important thing is, we should enable the APP Only Permission on the APP.
Hope this helps.
Happy Coding,
Sathish Nadarajan.


Leave a comment