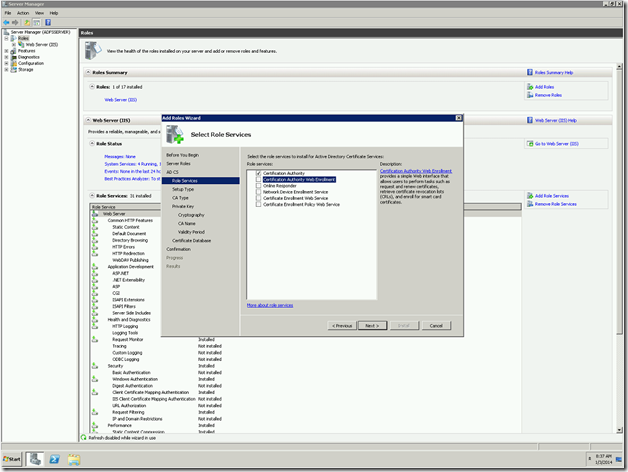
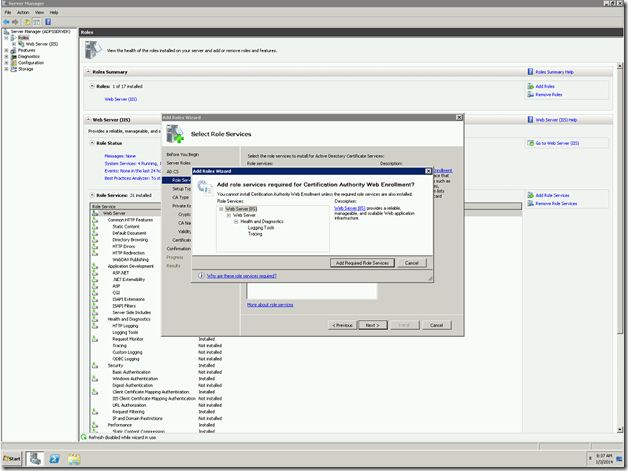
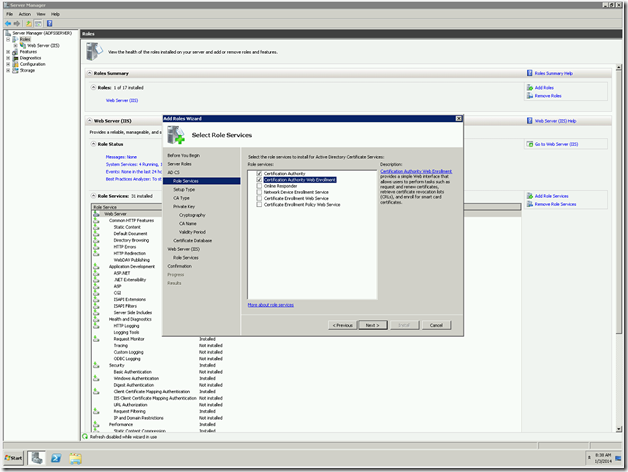
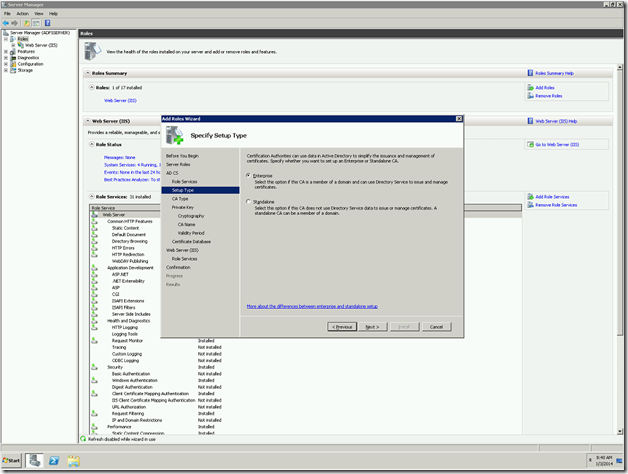
In some old articles, we saw about creating various types of WebApplications. Hope we are familiar with creating various web applications. Here, I faced another challenge. Thought of sharing that to the Community.
The requirement was something like, I want a web application, whose URL should be like https://MYDevelopmentSite.ss.loc:1000/Sites/MyDeveloperSite instead of https://Servername:1000/Sites/MyDeveloperSite. We may think, that, this is very simple. Even I thought the same thing. That is, this is going to be a straight forward one. But, the problem here is the site is SSL Enabled one.
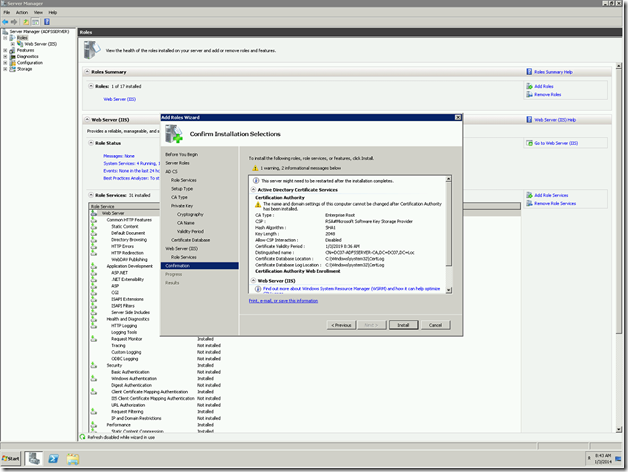
Let us see, how to create the web application using power shell and discuss about the problem and the error faced later.
$ap = New-SPAuthenticationProvider
New-SPWebApplication -Name "MyDevelopmentSite" -DatabaseName "WSS_Content_MyDevelopmentSite" -HostHeader "MyDevelopmentSite.DC07.Loc" -Port 4001 -ApplicationPool "MyDevelopmentSite" -ApplicationPoolAccount "DC07SPFarm" -URL "https://MyDevelopmentSite.DC07.Loc" -AuthenticationProvider $ap –SecureSocketsLayer
This will create the WebApplication with a host header. And the URL of the WebApplication would be https://MyDevelopmentSite.dc07.loc:4001/
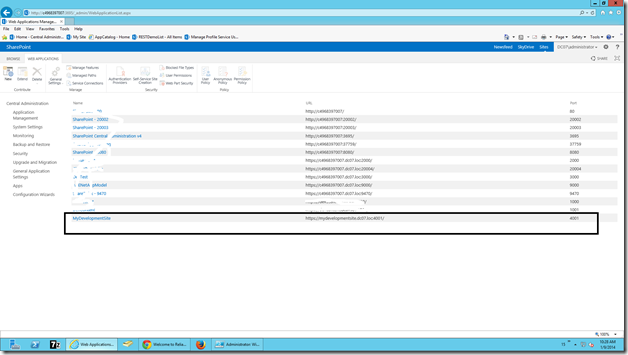
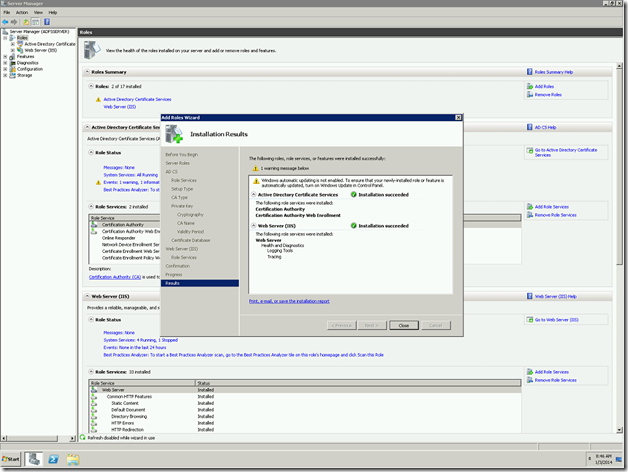
Let us go to the Central Administration to confirm whether the web app has been created or not.
Yes, it got Created.
Now, let us create a Sitecollection on this web application with the below script.
$template = Get-SPWebTemplate "PRODUCTCATALOG#0"
#$template
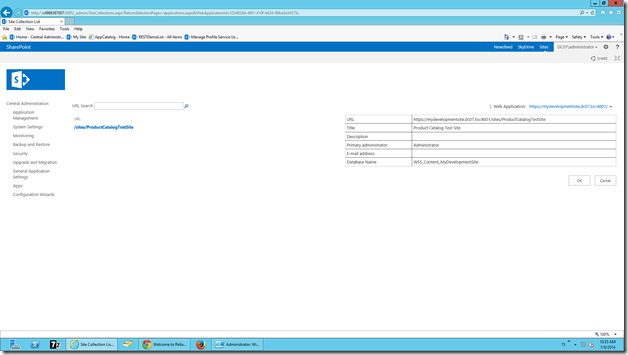
New-SPSite -Url "https://MyDevelopmentSite.DC07.Loc:4001/sites/ProductCatalogTestSite" -OwnerAlias "Administrator@dc07.loc" -Template $template -Name "Product Catalog Test Site"
The Site Collection has been created. Now, try accessing the Site Collection by the URL specified above.
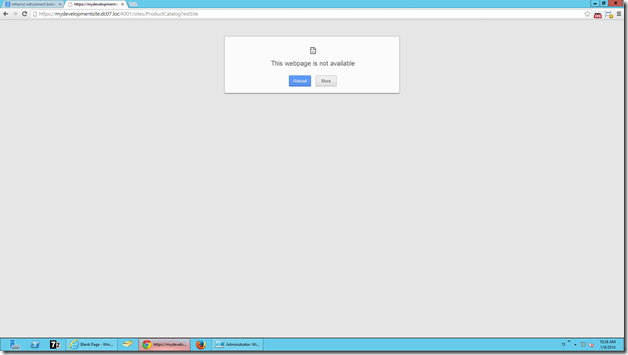
When try accessing this URL, We can see the below error message.
“The Webpage is not available” is a very weird exception. I know, everyone will get angry by seeing this exception. But once, we faced this, then this is a very simple exception.
The reason for this one is, this is SSL enabled. But till now, we haven’t binded any certificate for this web application. Let us do that by going to the IIS. The steps are as follows.
1. Open the inetmgr.
2. Create a SSL. To create, have a look on this article.
3. Bind the Certificate to the WebApplication Created. Refer here to do that.
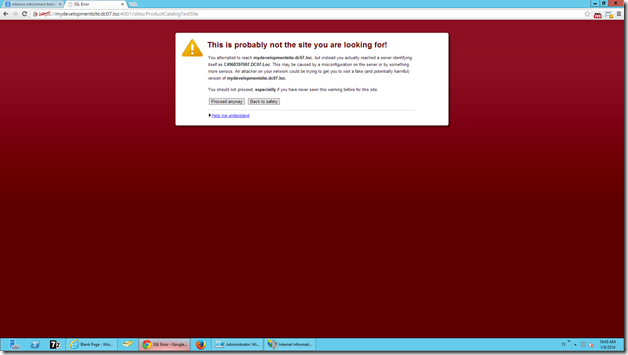
Once, we done with the binding and try opening the page, again, we may not have smile on our face. The below page will be thrown on our screen.
You attempted to reach mydevelopmentsite.dc07.loc, but instead you actually reached a server identifying itself as C4968397007.DC07.Loc. This may be caused by a misconfiguration on the server or by something more serious. An attacker on your network could be trying to get you to visit a fake (and potentially harmful) version of mydevelopmentsite.dc07.loc.
The screen would be something like
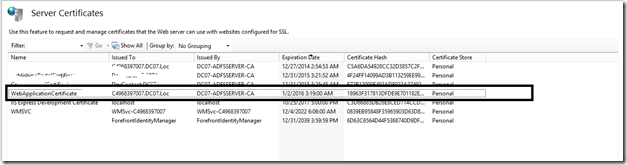
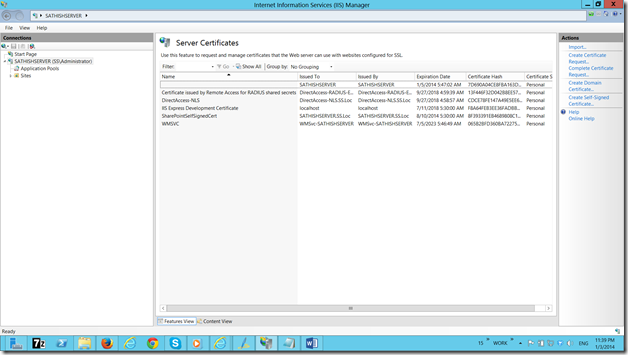
When we see this kind of exception, the immediate action item would regarding the Certificate. The Certificate, which we created from our IIS (Self-Signed Certificate) is the one which causes this exception. If you have a look at the Certificate, the “Issued To” would be the Machine Name.
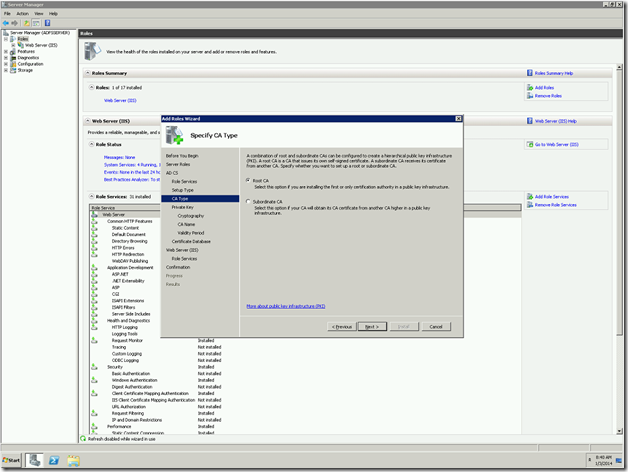
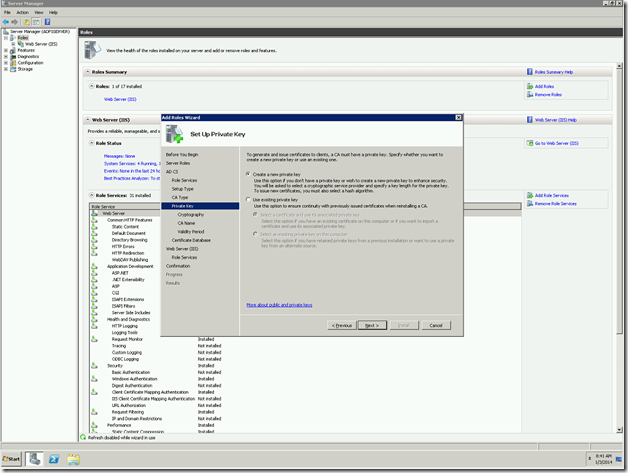
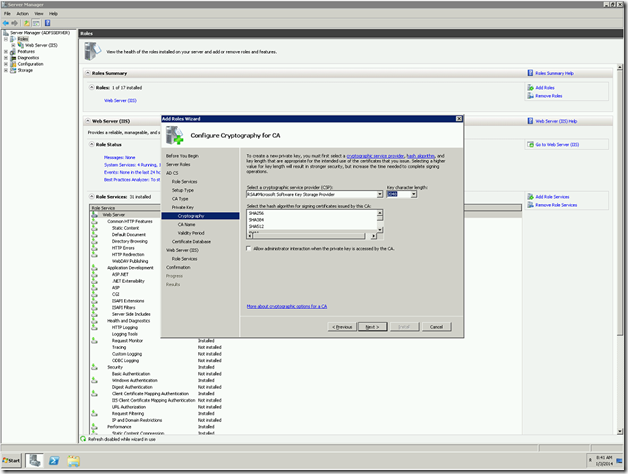
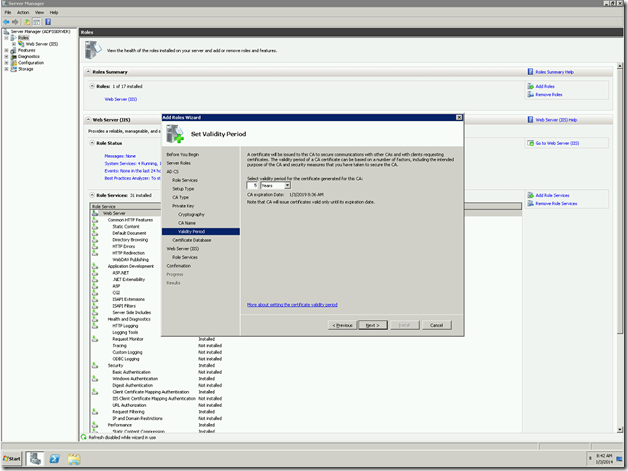
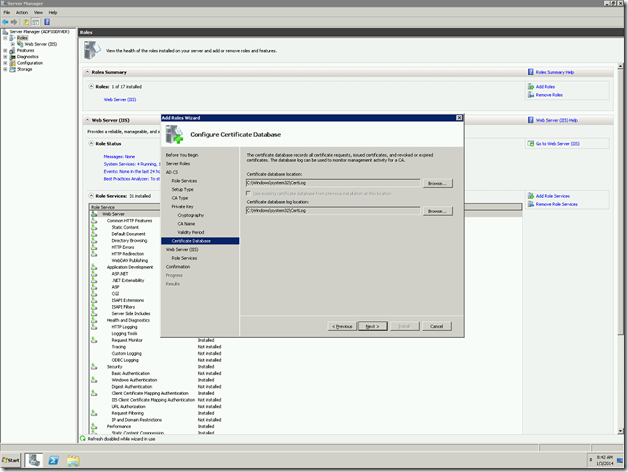
Now, we need to change the “Issued To” field. That we cannot do for a self-signed certificate. At that, time, there is no other go, that we need to create a Domain-Certificate. For that, we require the Domain Certificate Authority. We had already seen enough information about the Certificate Authority and the Domain Certificates in the previous posts.
For reference, I am giving the links here.
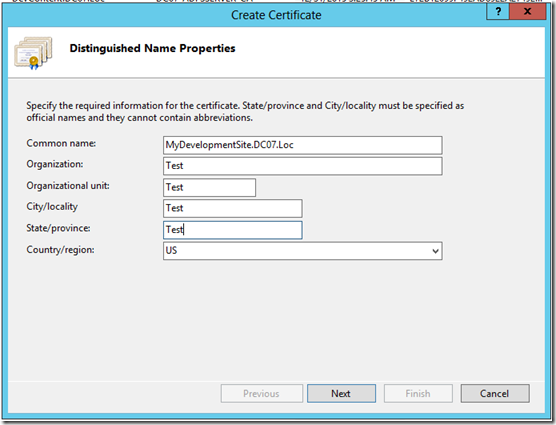
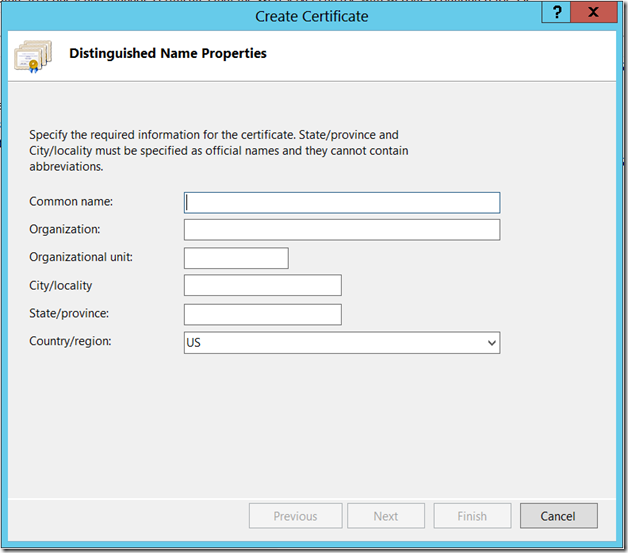
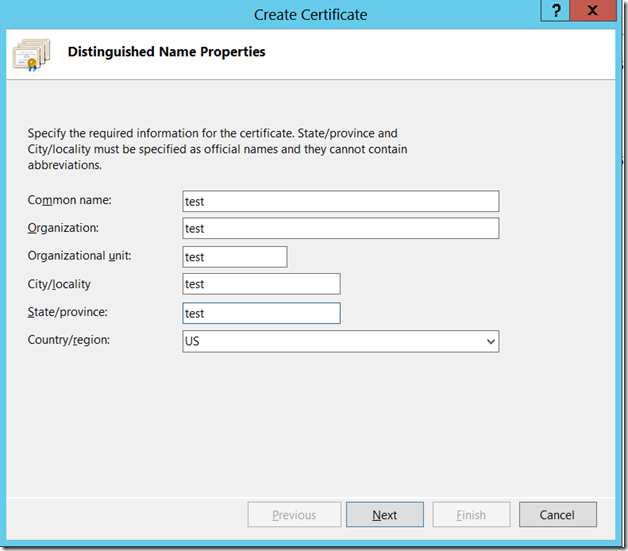
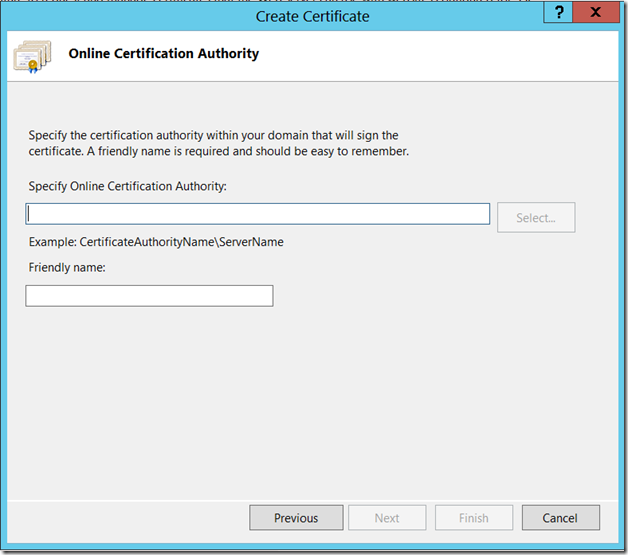
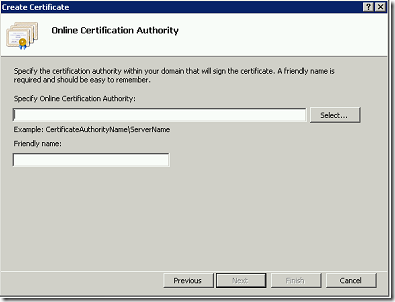
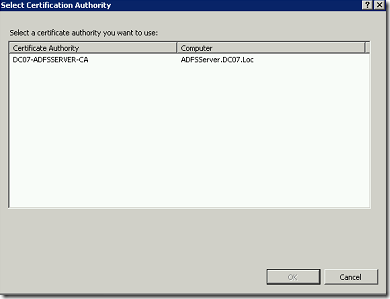
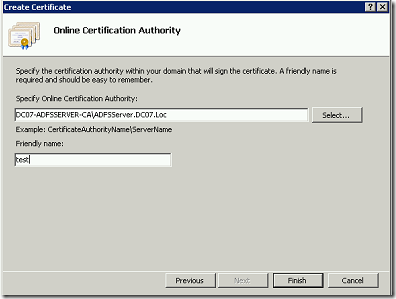
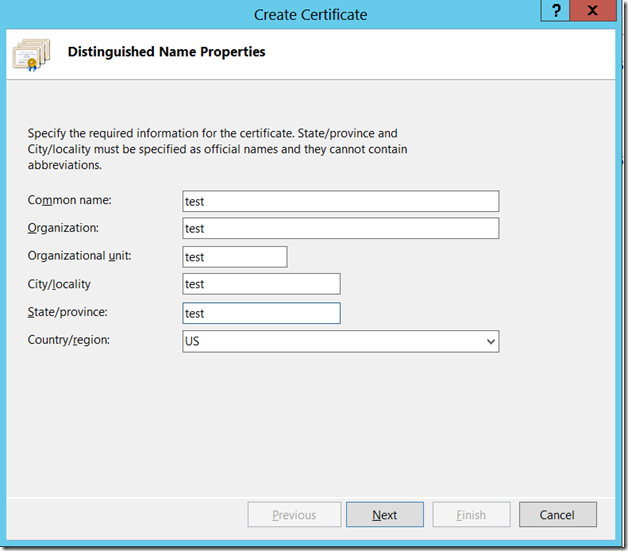
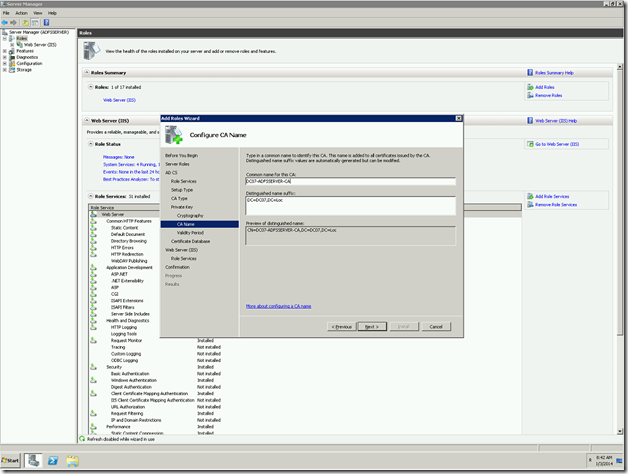
Let us Assume that, we are creating the Domain Certificate from IIS itself. Since that is the easiest approach. The important thing we need to note down is the “Common Name”
This should match the host header. This is the actual problem.
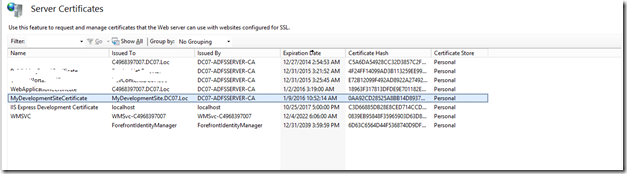
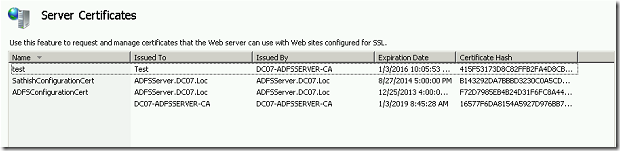
Then the created certificate would be
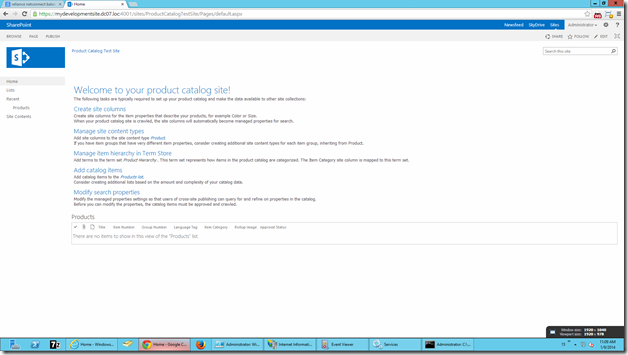
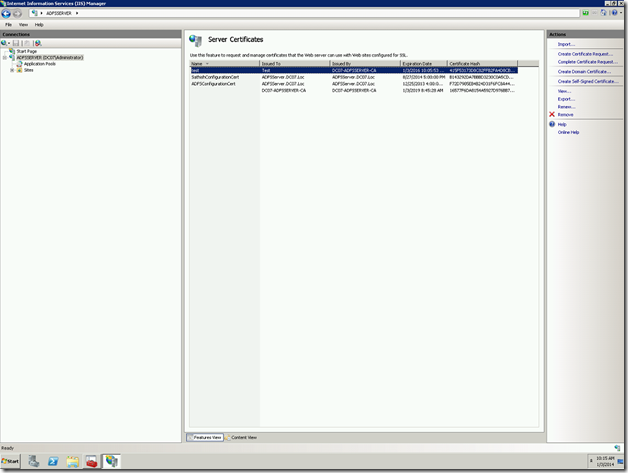
Now, map this certificate to the web application, which we created and try login.
Thus we created a web application with a host header and mapped that to a Domain Certificate.
In the next posts, we will see some more interesting requirements which I faced.
Happy Coding.
Sathish Nadarajan.

Leave a comment