In this article, let us see, how to create a web application, which gets authenticated using Form Based Authentication (FBA) against the Active Directory (LDAP). Usually, the Form Based Authentication will happen against the SQL DB. But in this case, let us see how the authentication is going to happen against the Active Directory.
As usual, let us go by Step by Step from the beginning.
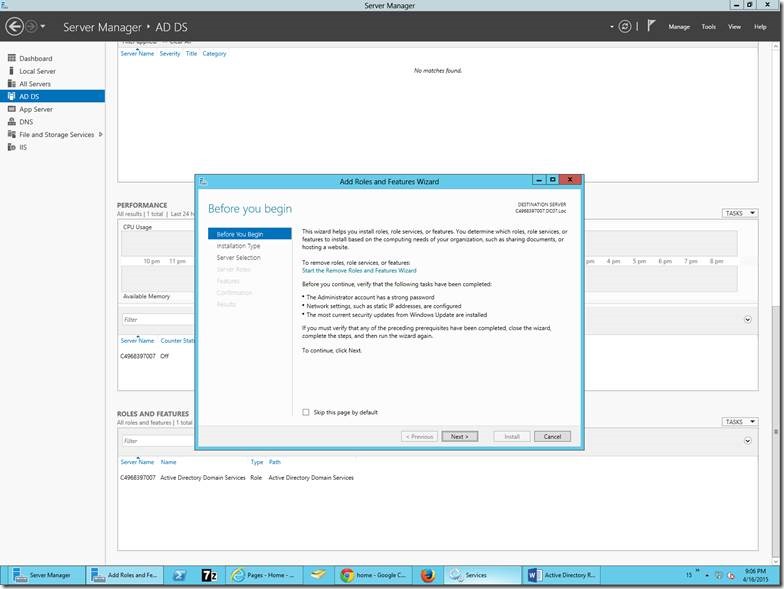
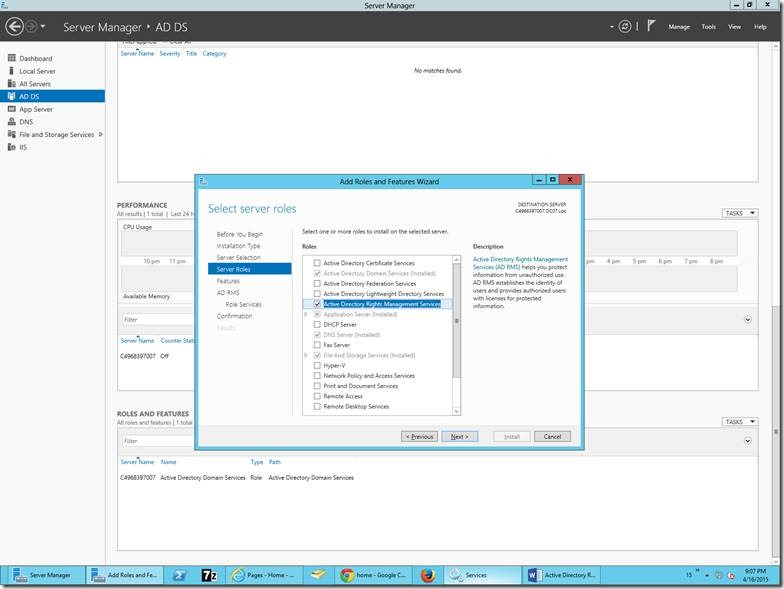
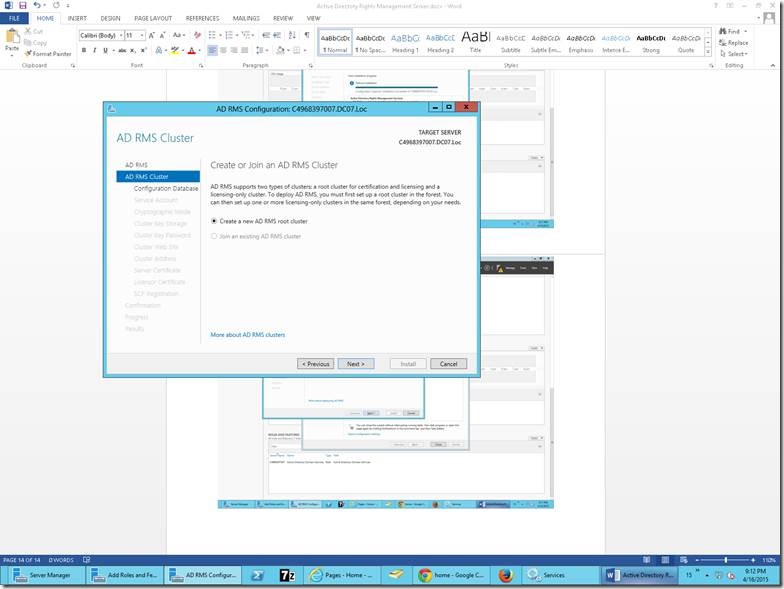
1. Create a Web Application from the Central Admin.
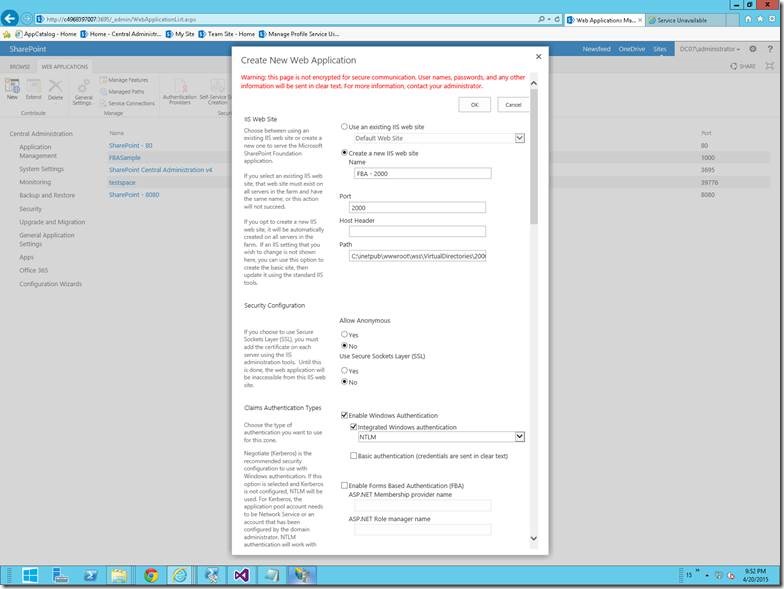
2. I have given the Name and the Port Number alone. The rest of the default settings, we will modify later. If we face any problem while creating the web application as mentioned on this post we can go with the PowerShell Script. The Script is as follows.
$ap = New-SPAuthenticationProvider
New-SPWebApplication -Name "FBA" -ApplicationPool "FBA" -ApplicationPoolAccount "DC07SPFarm" -URL "http://C4968397007:1000" -AuthenticationProvider $ap
$template = Get-SPWebTemplate "DEV#0"
$template
New-SPSite -Url http://C4968397007:1000/Sites/DeveloperSite -OwnerAlias "SSAdministrator" -Template $template
3. There are three config files we need to modify.
a. Web.Config of Central Administration
b. Web.Config of SecurityTokenServiceApplication
c. Web.Config of the Web Application which we created in the previous step.
4. Make sure that you have taken the backup of the Web.Config files before doing any changes. Because, that will help us a lot while roll back if anything goes wrong.
5. In the Central Admin add the following TAG under <Configuration ><System.Web> tag
<membership defaultProvider="AspNetSqlMembershipProvider">
<providers>
<add name="FBAMembershipProvider"
type="Microsoft.Office.Server.Security.LdapMembershipProvider, Microsoft.Office.Server, Version=15.0.0.0, Culture=neutral, PublicKeyToken=71e9bce111e9429c"
server="C4968397007.DC07.Loc"
port="389"
useSSL="false"
userDNAttribute="distinguishedName"
userNameAttribute="sAMAccountName"
userContainer="CN=Users,DC=DC07,DC=Loc"
userObjectClass="person"
userFilter="(ObjectClass=person)"
scope="Subtree"
otherRequiredUserAttributes="sn,givenname,cn" />
</providers>
</membership>
<roleManager enabled="true" defaultProvider="AspNetWindowsTokenRoleProvider" >
<providers>
<add name="FBARoleManager"
type="Microsoft.Office.Server.Security.LdapRoleProvider, Microsoft.Office.Server, Version=15.0.0.0, Culture=neutral, PublicKeyToken=71e9bce111e9429c"
server="C4968397007.DC07.Loc"
port="389"
useSSL="false"
groupContainer="DC=internal,DC=DC07,DC=Loc"
groupNameAttribute="cn"
groupNameAlternateSearchAttribute="samAccountName"
groupMemberAttribute="member"
userNameAttribute="sAMAccountName"
dnAttribute="distinguishedName"
groupFilter="(ObjectClass=group)"
userFilter="(ObjectClass=person)"
scope="Subtree" />
</providers>
</roleManager>
In the above Tags, modify the following attributes according to your environment. The values given here are based on the CloudShare Environment which I used for my demo purpose.
· <add name="FBAMembershipProvider"
· server="C4968397007.DC07.Loc" – To get this value, we can use the PowerShell
o [System.Net.DNS]::GetHostByName(”).HostName
· userContainer="CN=Users,DC=DC07,DC=Loc"
o I am using the Users Group from the Active Directory as my Canonical Name
· <add name="FBARoleManager"
· server="C4968397007.DC07.Loc" – To get this value, we can use the PowerShell
o [System.Net.DNS]::GetHostByName(”).HostName
· groupContainer="DC=internal,DC=DC07,DC=Loc"
o This, give the first DC as Internal and the rest of the DC depends on your Domain Name.
6. Now, we have completed the modifications on the Central Admin Web.Config.
7. Let us go to the SecureTokenServiceApplication Web.Config
8. If does not know the exact port number, then go to the IIS. And follow the steps as shown in the screen shots.
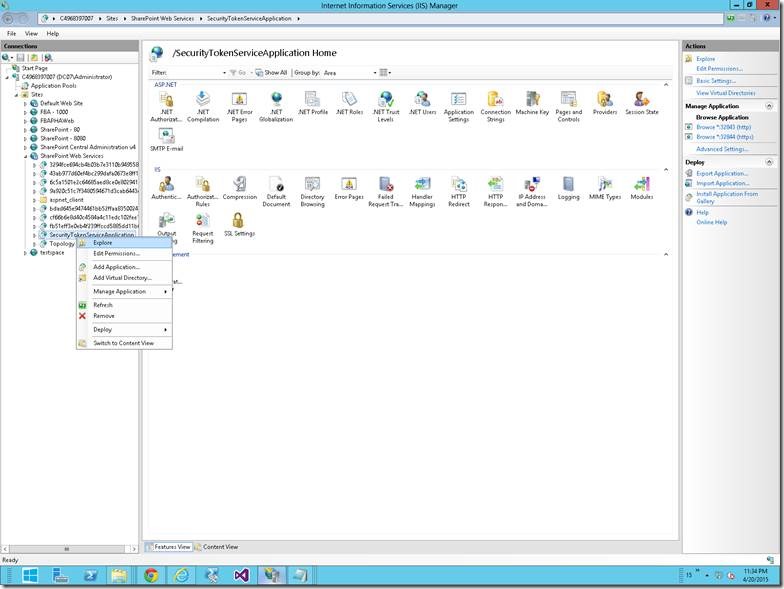
On the SharePoint WebServices Site, select the Security Token Service Application Application and right Click, Explore. By default the location would be C:\Program Files\Common Files\Microsoft Shared\Web Server Extensions\15\WebServices\SecurityToken
9. Again, take a back up of the web.config and start making the changes.
10.Add the following entry under the <Configuration ><System.Web>
<membership>
<providers>
<add name="FBAMembershipProvider"
type="Microsoft.Office.Server.Security.LdapMembershipProvider, Microsoft.Office.Server, Version=15.0.0.0, Culture=neutral, PublicKeyToken=71e9bce111e9429c"
server="C4968397007.DC07.Loc"
port="389"
useSSL="false"
userDNAttribute="distinguishedName"
userNameAttribute="sAMAccountName"
userContainer="CN=Users,DC=DC07,DC=Loc"
userObjectClass="person"
userFilter="(&(ObjectClass=person))"
scope="Subtree"
otherRequiredUserAttributes="sn,givenname,cn" />
</providers>
</membership>
<roleManager enabled="true" >
<providers>
<add name="FBARoleManager"
type="Microsoft.Office.Server.Security.LdapRoleProvider, Microsoft.Office.Server, Version=15.0.0.0, Culture=neutral, PublicKeyToken=71e9bce111e9429c"
server="DC07.Loc"
port="389"
useSSL="false"
groupContainer="DC=internal,DC=DC07,DC=Loc"
groupNameAttribute="cn"
groupNameAlternateSearchAttribute="samAccountName"
groupMemberAttribute="member"
userNameAttribute="sAMAccountName"
dnAttribute="distinguishedName"
groupFilter="(ObjectClass=group)"
userFilter="(ObjectClass=person)"
scope="Subtree" />
</providers>
</roleManager>
11. The parameters to change are same as that of the Central Admin Web.Config. The highlighted values are based on the Cloud Share Environment which I used for the demo purpose.
12. Now, let us go to the Third Web.Config file changes.
13. In the <Configuration> section, find the <system.web> section.
14. Find the <membership defaultProvider="i"> section and add the following example entry to the <Providers> section:
<add name="FBAMembershipProvider" type="Microsoft.Office.Server.Security.LdapMembershipProvider, Microsoft.Office.Server, Version=15.0.0.0, Culture=neutral, PublicKeyToken=71e9bce111e9429c"
server="DC07.Loc"
port="389"
useSSL="false"
userDNAttribute="distinguishedName"
userNameAttribute="sAMAccountName"
userContainer="CN=Users,DC=DC07,DC=Loc" userObjectClass="person" userFilter="(&(ObjectClass=person))"
scope="Subtree"
otherRequiredUserAttributes="sn,givenname,cn" />
15. Find the <roleManager defaultProvider="c" enabled="true" cacheRolesInCookie="false"> section and add the following example entry to the <Providers> section:
<add name="FBARoleManager"
type="Microsoft.Office.Server.Security.LdapRoleProvider, Microsoft.Office.Server, Version=15.0.0.0, Culture=neutral, PublicKeyToken=71e9bce111e9429c"
server="C4968397007.DC07.Loc"
port="389"
useSSL="false"
groupContainer="DC=internal,DC=DC07,DC=Loc"
groupNameAttribute="cn"
groupNameAlternateSearchAttribute="samAccountName"
groupMemberAttribute="member"
userNameAttribute="sAMAccountName"
dnAttribute="distinguishedName"
groupFilter="(&(ObjectClass=group))"
userFilter="(&(ObjectClass=person))" scope="Subtree" />
16. With the above changes, let us come back to the Central Admin again.
17. Go to Manage Web Application.
18. Select the Web Application on which our Site Collection resides.
19. Click on the “Authentication Providers” on the Ribbon.
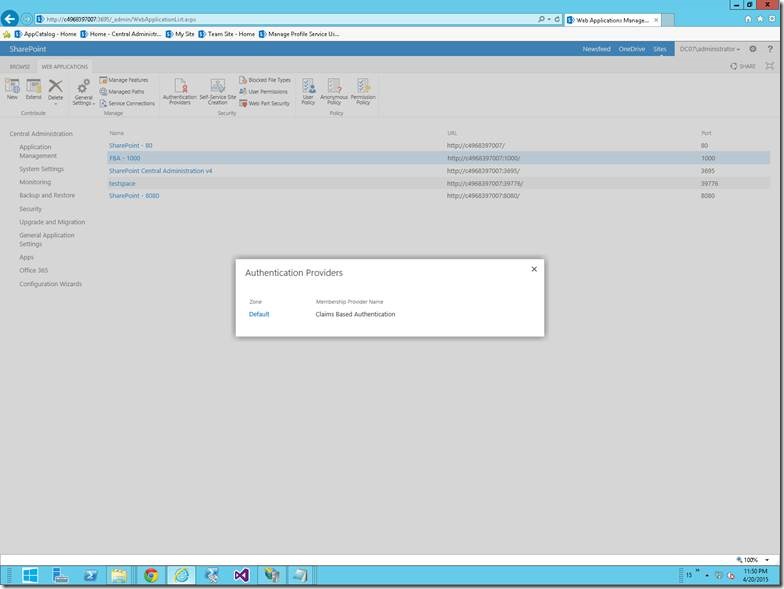
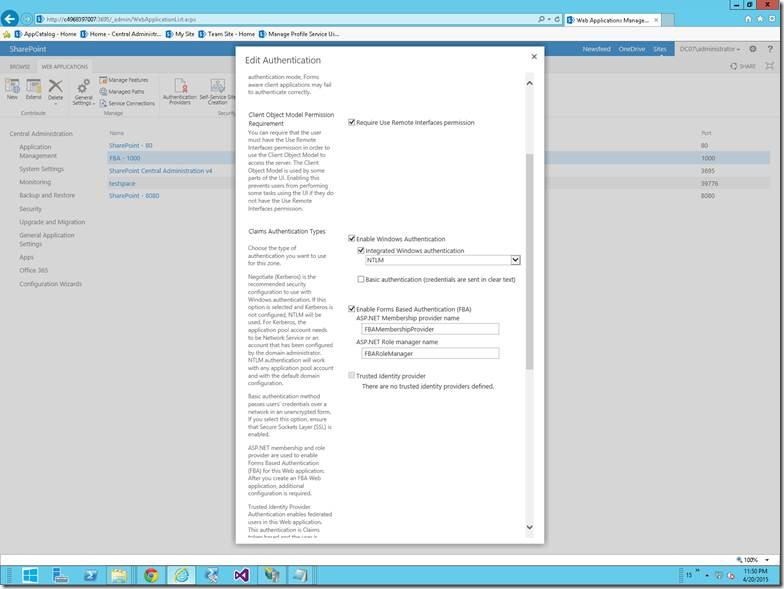
20. Click on the Default HyperLink
21. On the below screen, Check the “Enable Form Based Authentication”
22. And give the proper values for the Provider and the role Manager.
23. With this, let us try to open the Site Collection. Here my site collection is http://c4968397007:1000/sites/developerSite
24. The login screen would be something like,
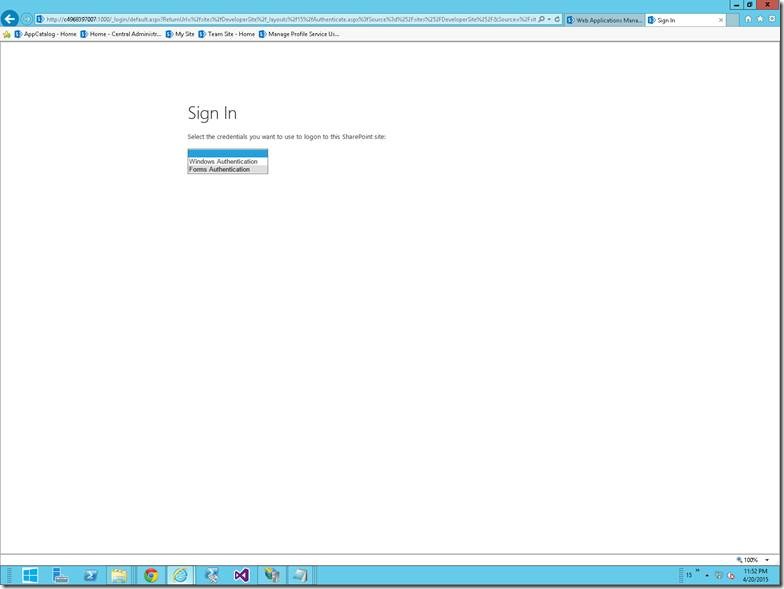
25. On Selecting the Forms Authentication, you will be redirected to a default login page.
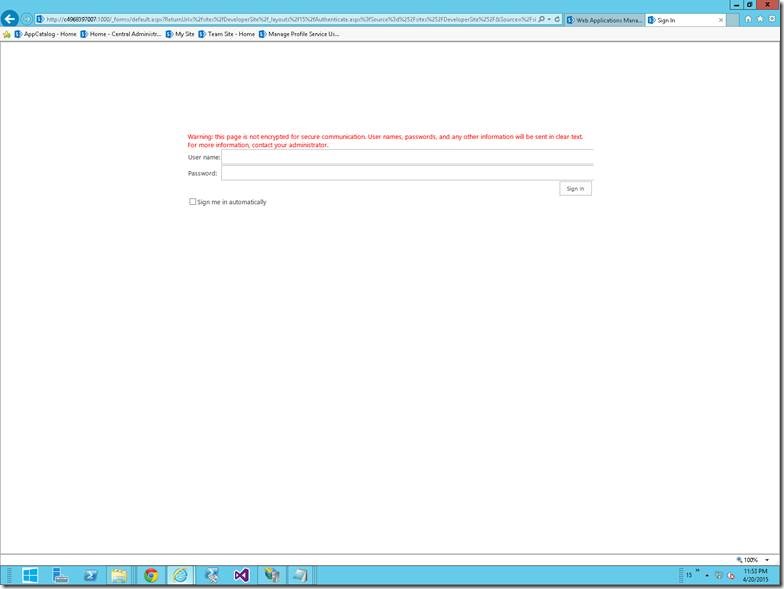
26. Enter the appropriate credentials and this screen will authenticate you against the Active Directory using the LDAP Services.
Hope this would have helped to implement the Form Based Authentication using Active Directory in SharePoint 2013. In the coming article, let us see, how to use a custom sign in page, instead of this blank white screen given by SharePoint.
Download the Sample Config Files Here
Happy Coding,
Sathish Nadarajan.







Leave a comment