All of us know the importance of Certificate while in development environment as well in the customer’s environment. Being a developer, we don’t bother about the customer environment’s Certificates. But, while developing itself, we will be required to deal with the certificates frequently. For Example, even for creating a HTTPS site, we require certificates.
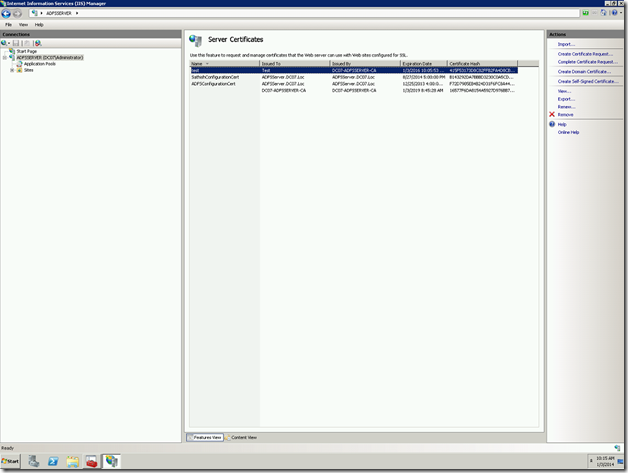
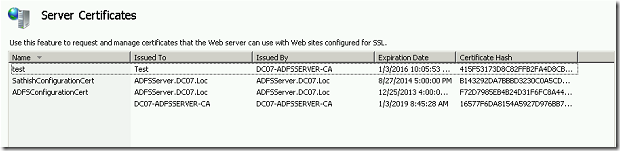
Regarding this, we had already seen, how to create a self-signed certificate from IIS in this post. But, the problem which we faced here is, the validity of the Certificate. The default validity of the self-signed certificates are one year. After one year, there is no option to renew or extend the validity. Even I couldn’t see any option for the AutoCertificateRollover also. (We can discuss about them in some other posts.)
At the same time, for the development, we cannot buy any certificate for cost also. At this scenario, if we have a Windows Server 2008 R2 machine (or any other Server OS can help. Since, I used Windows Server 2008 R2, I am explaining about that), we can convert our server into a Certificate Authority Server, and get certificates from that itself. We can renew, and we can choose any templates etc., There are much more options are there.
Let us see how to install the Active Directory Certificate Services first. As usual, the step by step procedure are as follows.
1. Open the Server Manager
2. Select the Roles. And Add Roles.
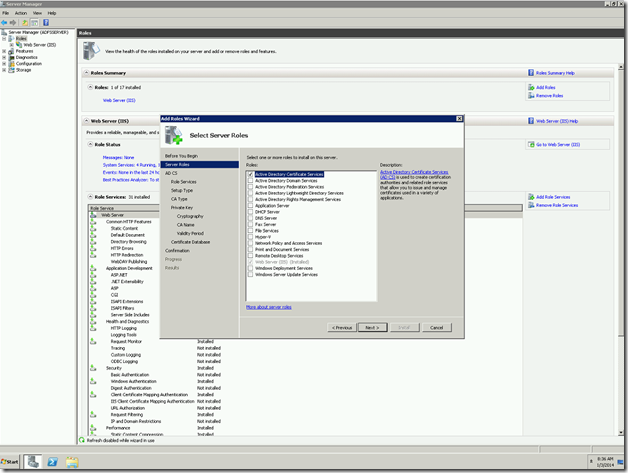
3. Select the Active Directory Certificate Services
4. The installation Wizard will begin
5. Select the Services. The basic things we require for our need is, Certificate Authority and Certification Authority Web enrollment
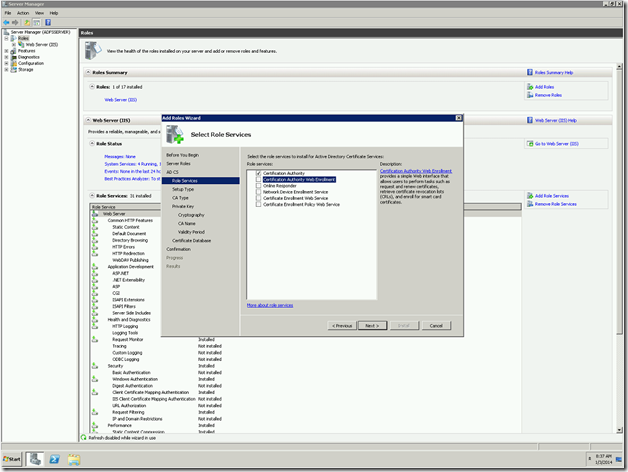
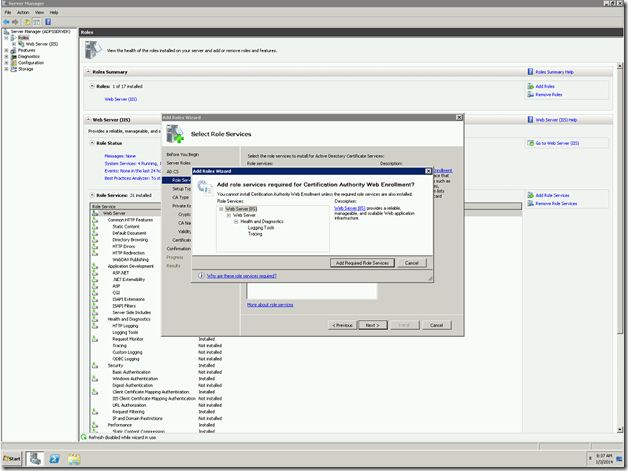
6. To install, the Web Enrollment Service, there are certain IIS related Services needs to be installed. Click on Add Required Role Services.
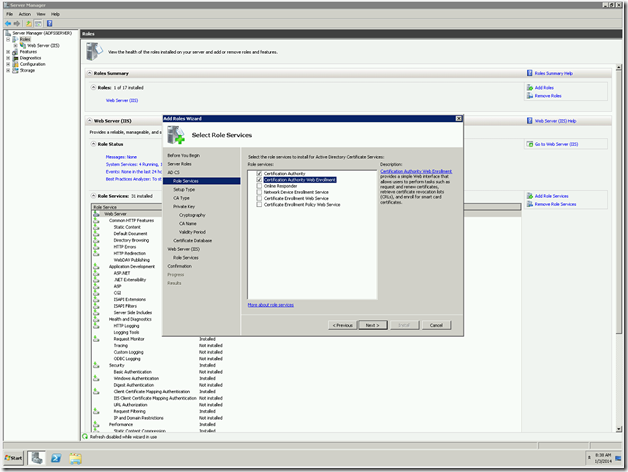
7. Now, go to the next screen
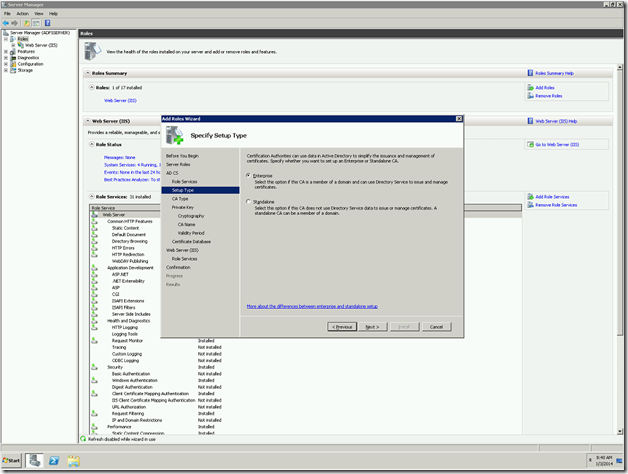
8. Select the Enterprise, since we are going to use the existing Active Directory
9. Select the Root CA. This Certification Authority is going to be the Root for any other sub Certification Authority in future. As for as concerning the development machine, we don’t need to worry about this. We can proceed with Root CA
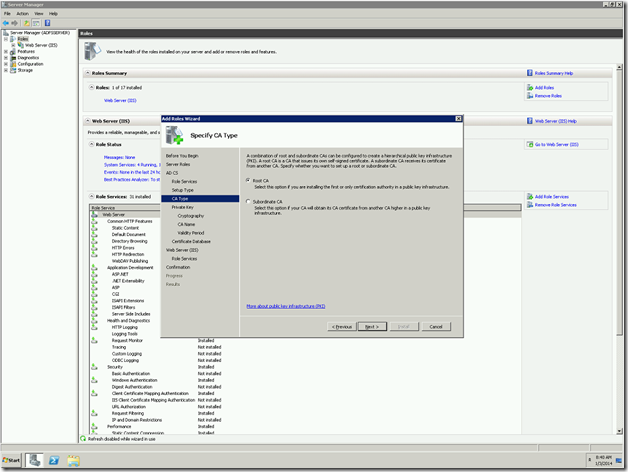
10. Select the New Private Key
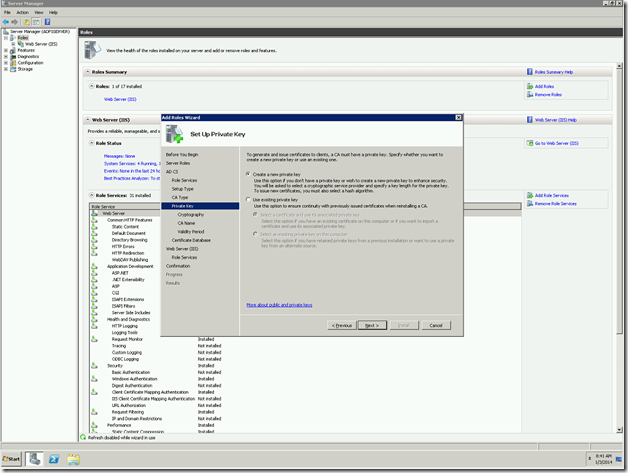
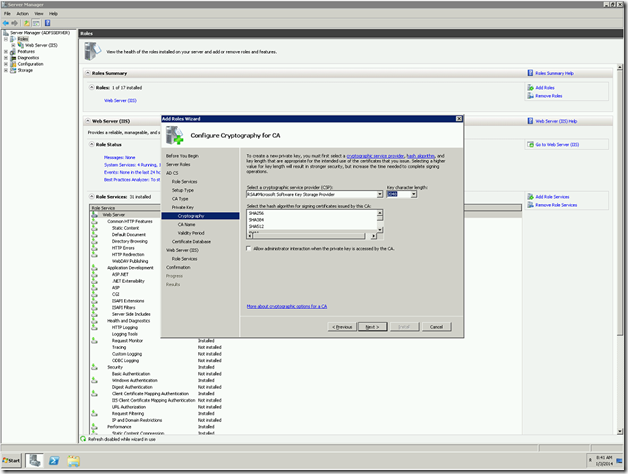
11. The encryption methods. Leave as by default. The only thing to be noted here is the Key Character Length. For a safer side, always keep the length not less than 2048.
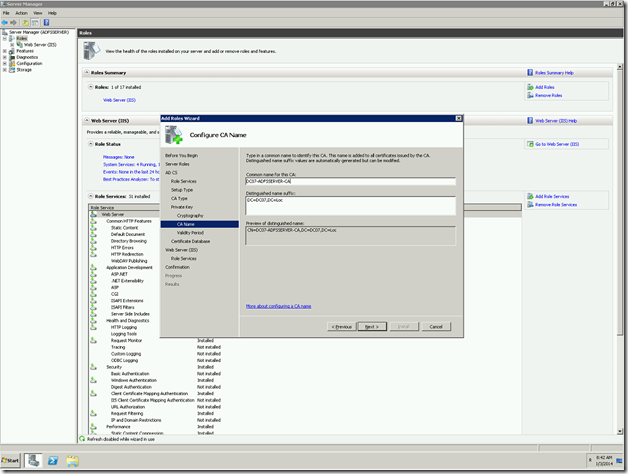
12. Give the name of the CA and the Certificate prefixes etc., Mostly keep as it as default.
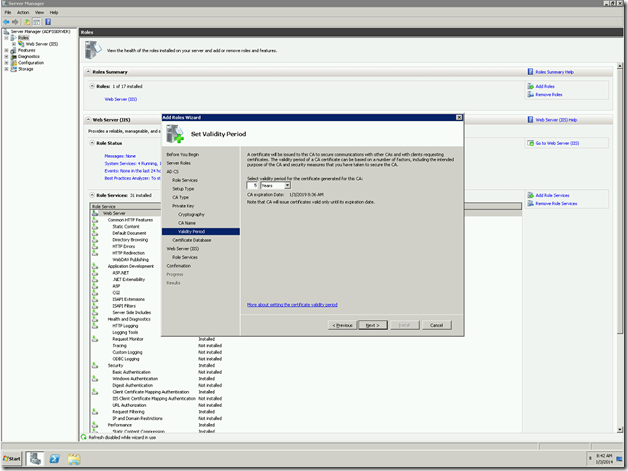
13. Validity of the Certificate. Give as you require. Even, if you give a lesser value, we can renew the certificate.
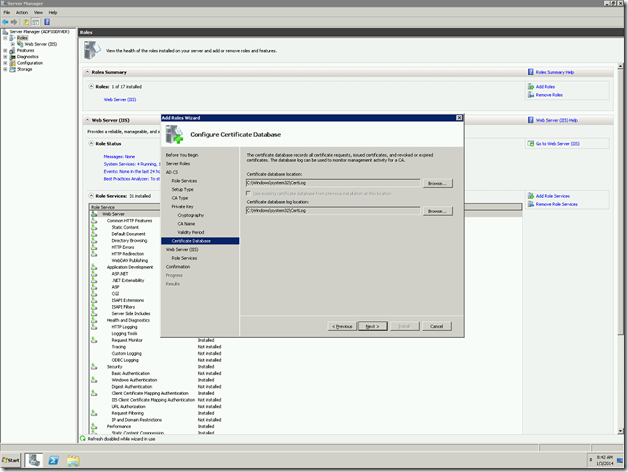
14. Location of the database files.
15. Confirm and proceed with installation.
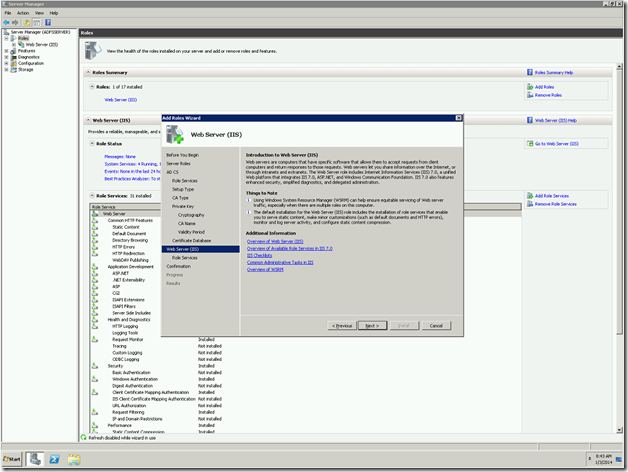
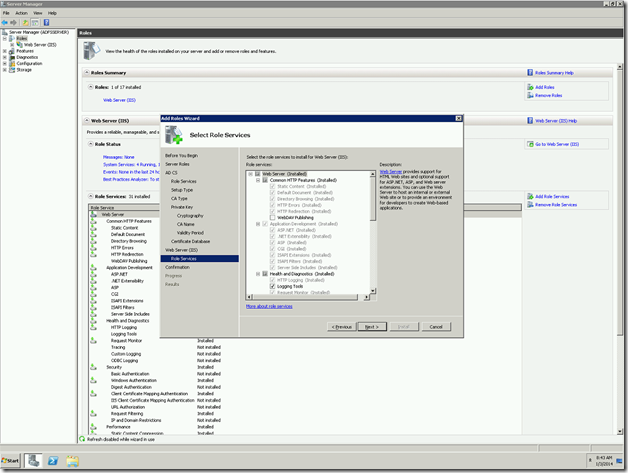
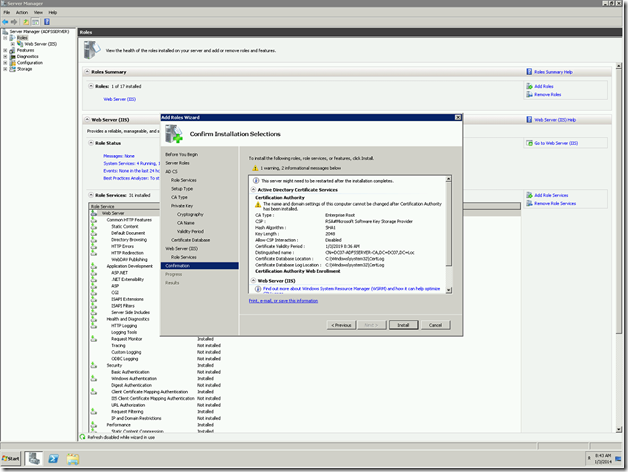
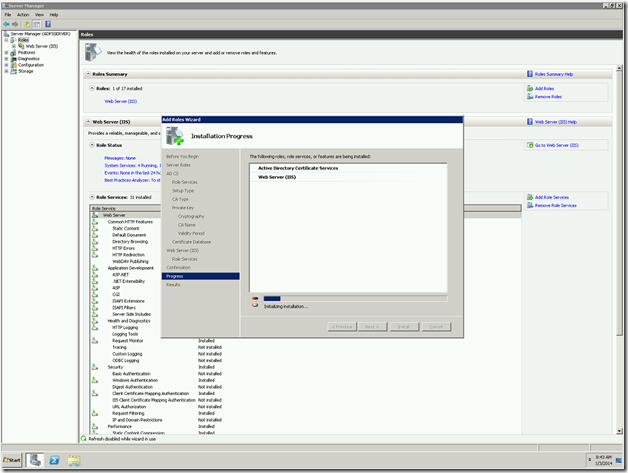
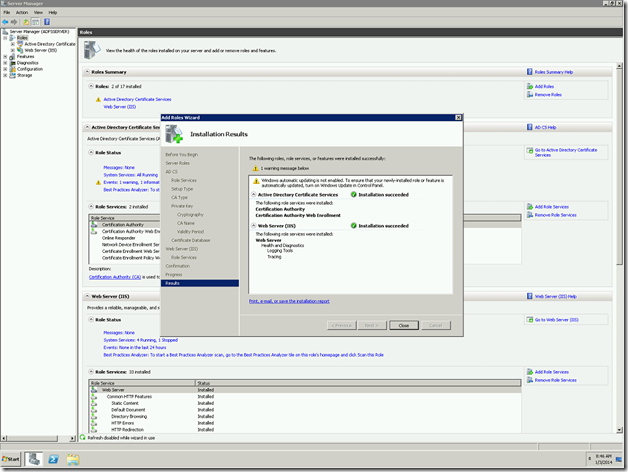
Verifying the Installation.
Once the installation got succeed, we need to verify. To verify that, we can go to Server manager again and see the Roles has been added.
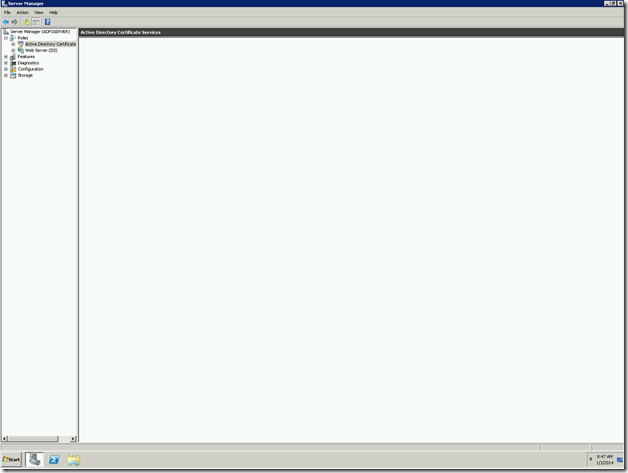
To verify against the Certification Authority, the following steps will help us.
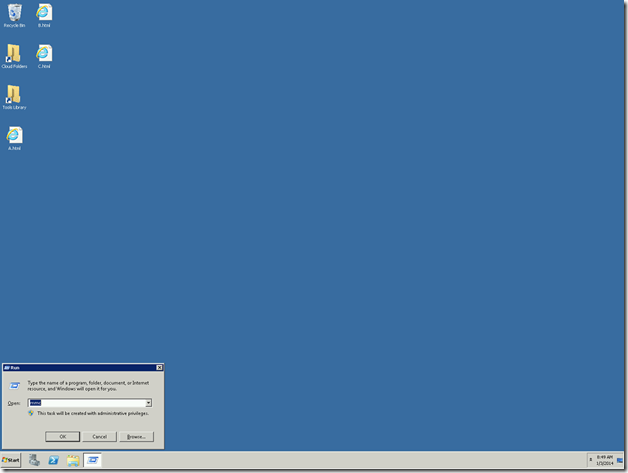
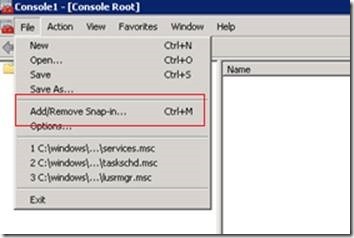
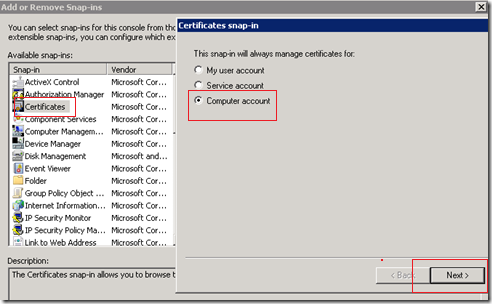
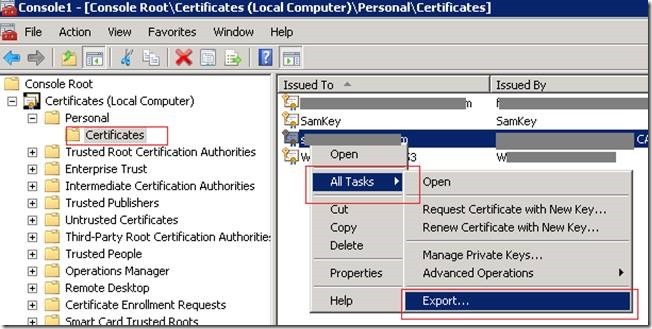
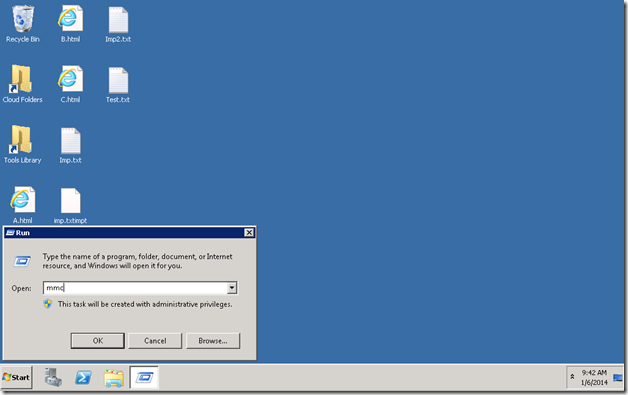
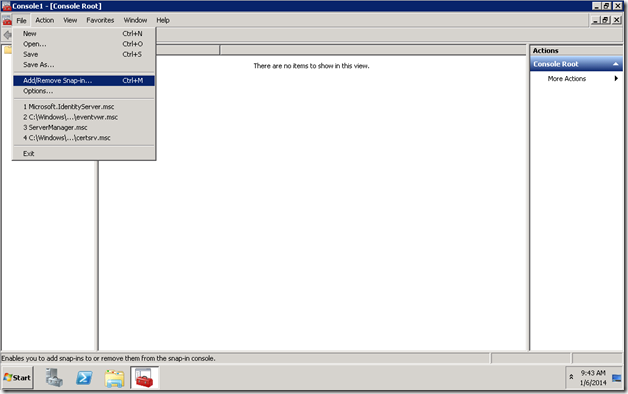
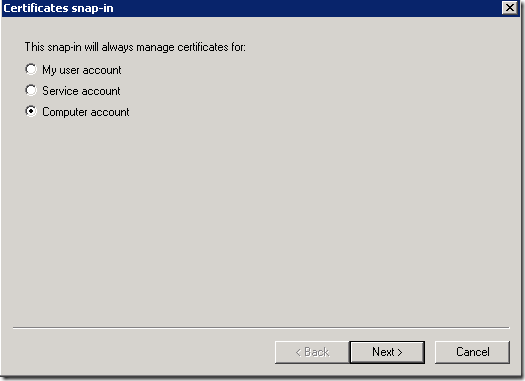
1. Go to Run and type MMC
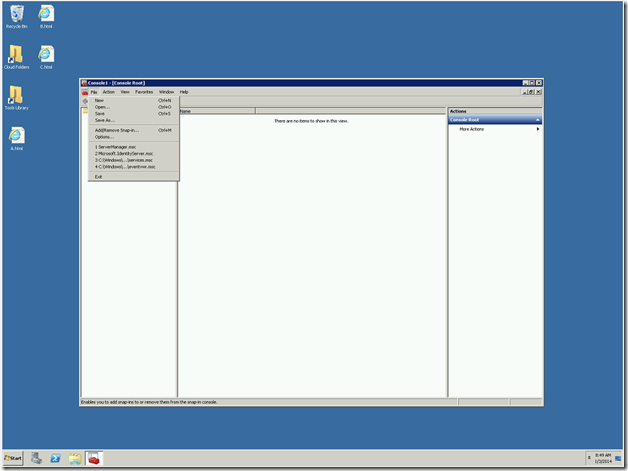
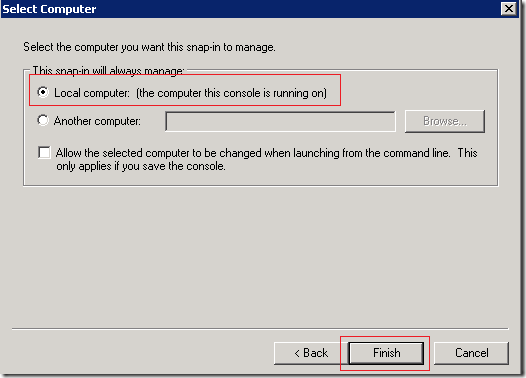
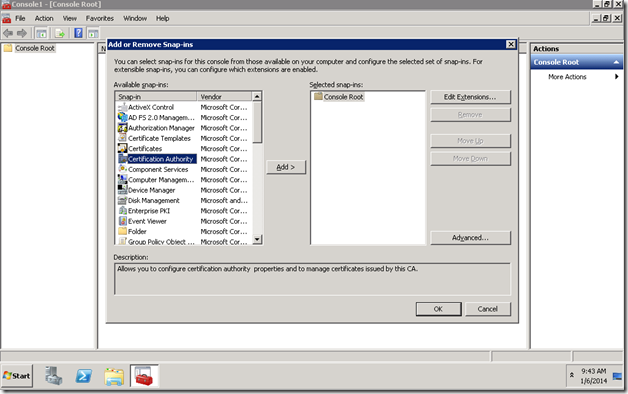
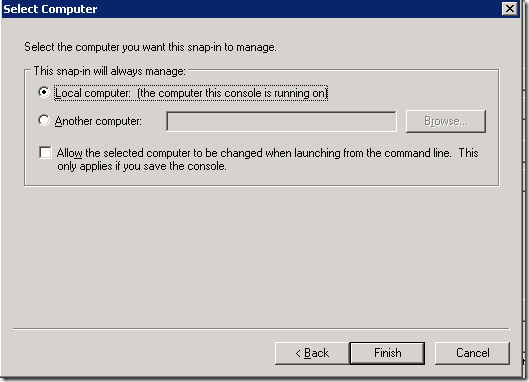
2. Management Console will open. On that, Add Snapin.
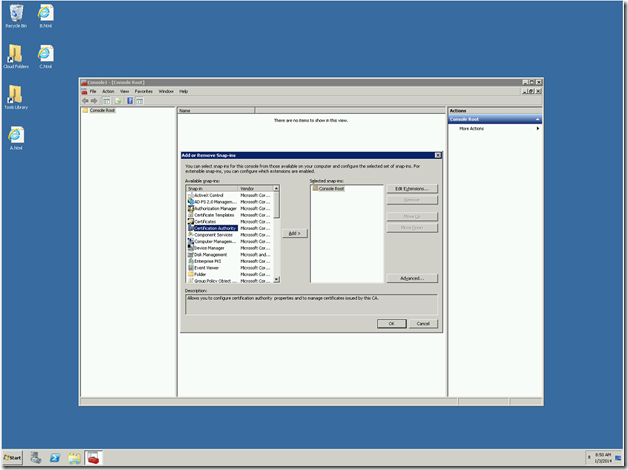
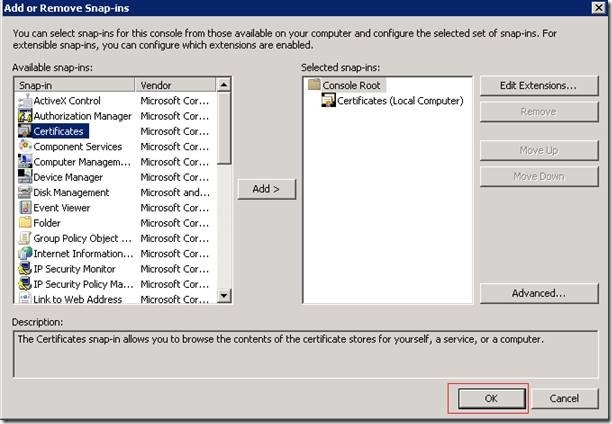
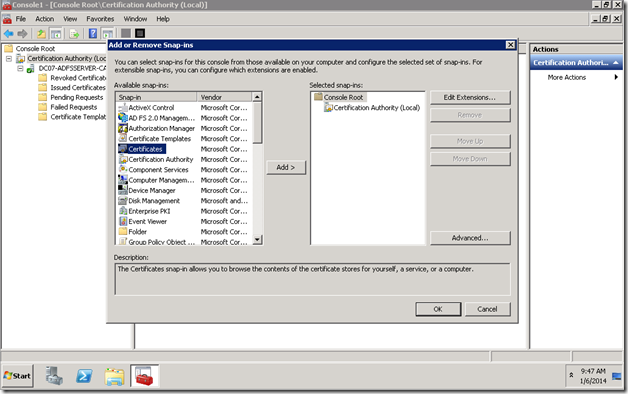
3. Add Certification Authority and select Local.
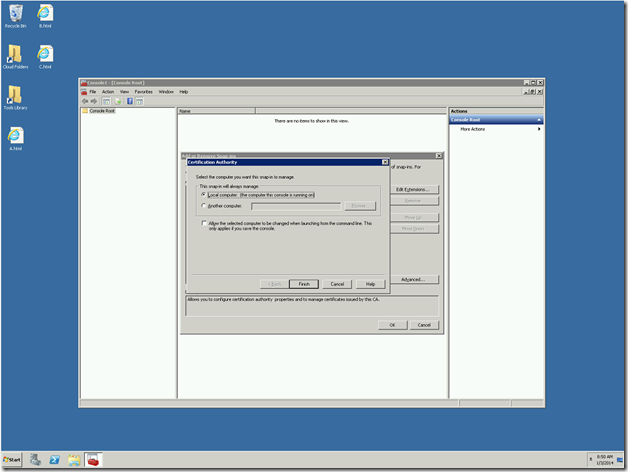
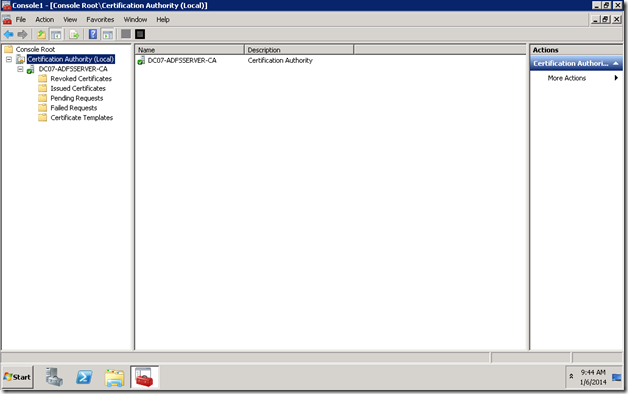
4. It will get added.
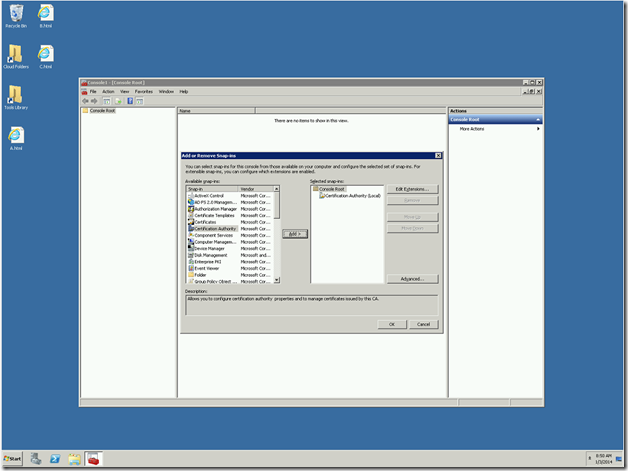
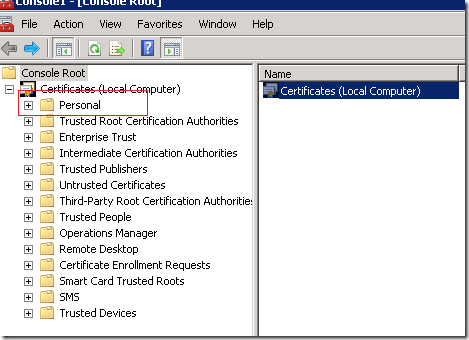
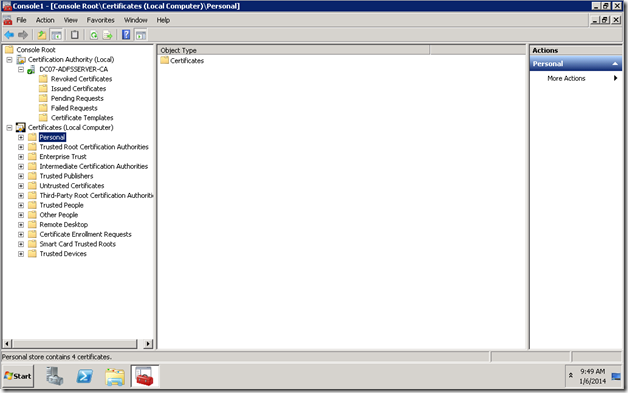
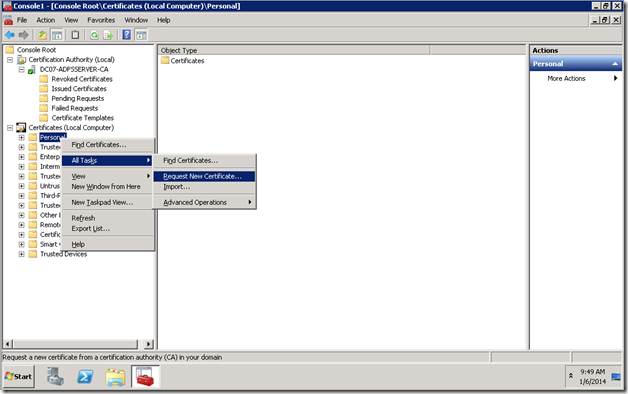
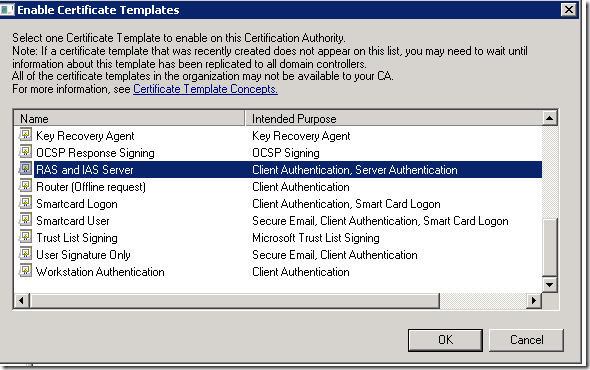
5. Now, you can see the entire certificates which were issued, pending requests, Certificate templates etc.,
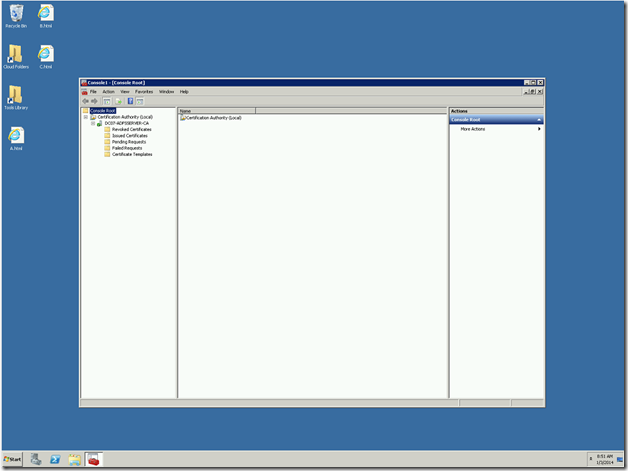
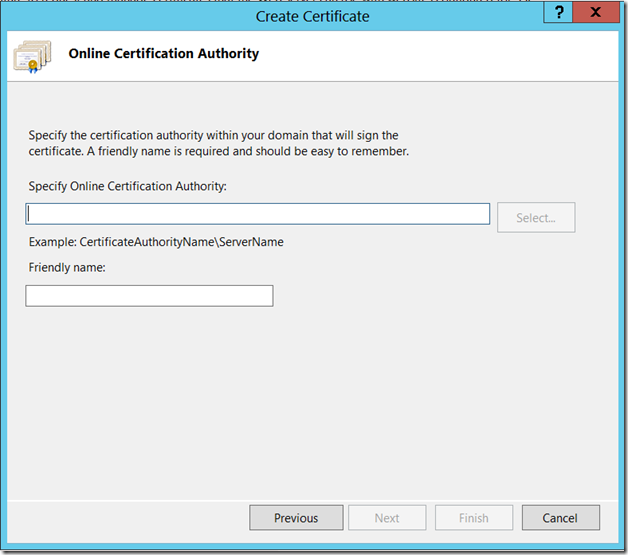
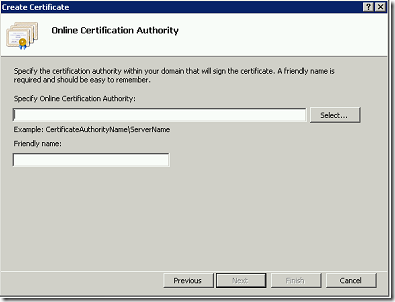
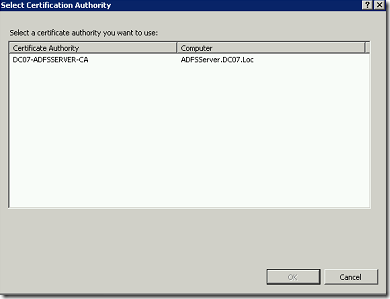
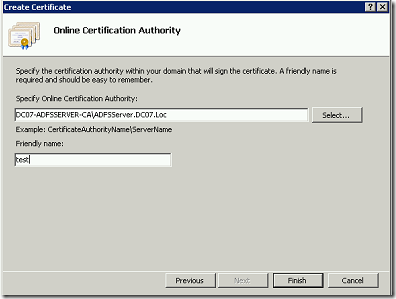
We can see, how to create a certificate using this Certification Authority in the consecutive posts.
Happy Coding.
Sathish Nadarajan.





























Leave a comment